La llegada de la nueva versión de Java 16 a Minecraft dejó al actual PreLauncher v7 fuera de servicio, por lo que tuvimos que empezar a trabajar en una actualización para corregir errores e incluir la compatibilidad con la nueva versión de Java.
El «Pre-Launcher», como lo hemos llamado, es la aplicación encargada de descargar y actualizar el launcher para mantenerlo siempre en la última versión disponible. Con esta aplicación no tienen que preocuparse por descargar el launcher manualmente cada vez que se publique una nueva actualización, ya que el PreLauncher se encargará de esa tarea.
Después de mucho tiempo alejados del proyecto, hemos vuelto, y ya estamos trabajando en una nueva versión renovada del LauncherFenix, ¿o quizás tenga otro nombre? ya veremos. Hasta tanto seguiremos manteniendo funcional esta versión del launcher para continuar brindando el servicio a la comunidad mientras seguimos trabajando.
¿Que incluye esta nueva versión?
La última versión disponible del launcher al día de la fecha en que se realiza esta publicación, es la versión 5.7.9 la cual incluye, entre otras características, las siguientes:
- Compatible con todas las versiones del Minecraft, tanto las versiones estables (Releases) como las de prueba (Snapshots) y las versiones antiguas (Alphas, Betas).
- Compatible con las versiones de Java más utilizadas, desde Java 7 hasta Java 16, para no dejar afuera a los usuarios que poseen PC de bajos recursos y continúan jugando a versiones antiguas de Minecraft.
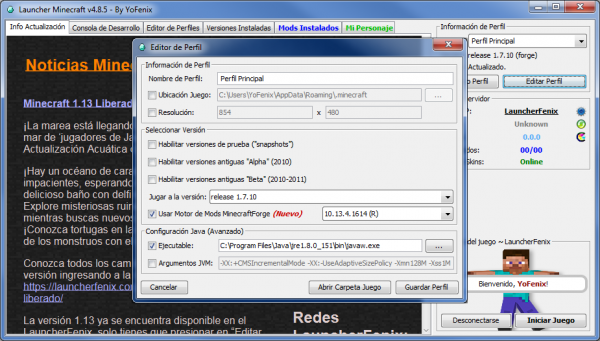
- Puedes cambiar entre las distintas versiones del juego seleccionándolas desde el panel «Editar Perfil» y se descargará automáticamente.
- Permite crear perfiles con distintos usuarios y configuraciones para cambiar rápidamente entre ellos.
- Ofrece la posibilidad de seleccionar la versión de Java con la que se desea iniciar el juego y personalizar sus parámetros internos. («Argumentos JVM»).
- Instalar MinecraftForge es tan sencillo como marcar una casilla en las opciones del launcher. (Esta opción les permitirá instalar mods para el juego).
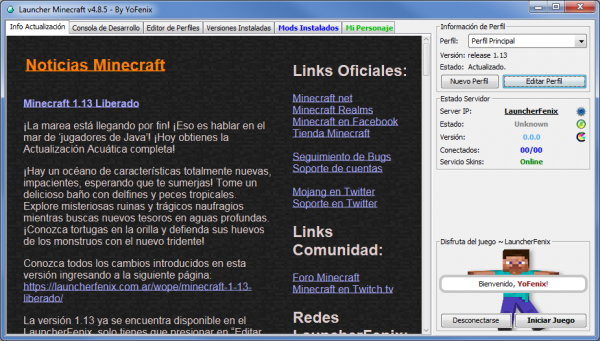
- Cuenta con una pestaña de noticias con la que podrán mantenerse al tanto de las modificaciones que se realizan sobre el launcher, una consola en la que podrán ver el proceso interno que realiza el launcher y los errores que surjan durante dicho proceso, un editor de perfiles desde donde podrán modificar o borrar los perfiles que tienen creados, y un editor de versiones en donde verán las versiones del Minecraft que posee instaladas.
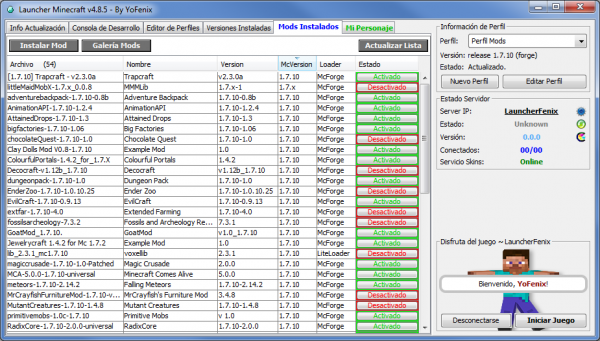
- Dispone de un panel dedicado a la instalación y manipulación de los Mods que se utilizarán en el juego. Este panel les permitirá instalar mods, quitarlos, activarlos y desactivarlos según lo necesiten. Incluso podrán crear varios perfiles y activar los mods que quieran en cada perfil.
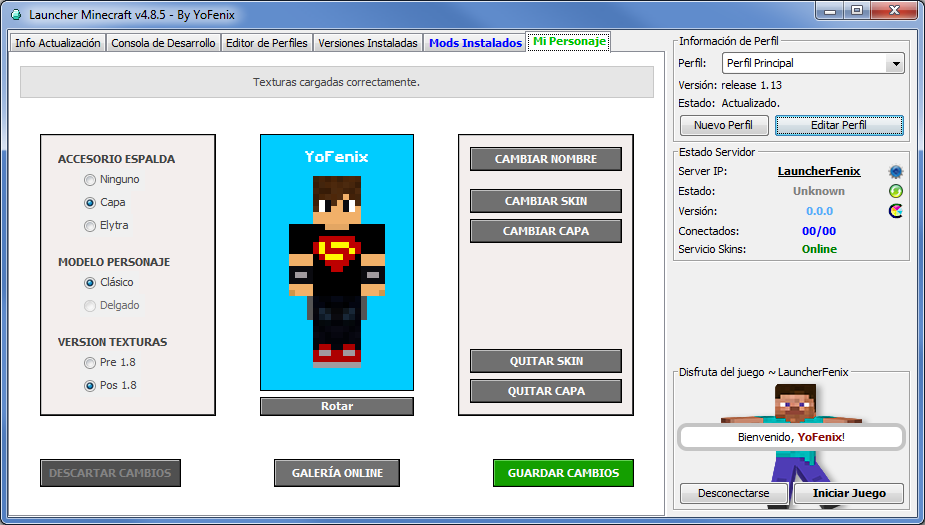
- Dispone también de un panel con el que podrán personalizar su personaje cambiándole el nombre, colocándole una skin, una capa y una elytra personalizada. (Para usar esta opción deberán iniciar sesión en el launcher con su cuenta de esta página).
- Posee un pequeño panel llamado “Estado Servidor” en dónde podrán consultar el estado del servidor que deseen sin tener que iniciar el juego y también podrán ver el estado del servidor de skins que utiliza el launcher.
- El launcher está disponible en dos formatos, el formato JAR, funcional en la mayoría de los sistemas operativos para PC y el formato EXE, exclusivo para el Sistema Operativo Windows.
- Y lo más importante para muchos, ES TOTALMENTE GRATIS! 😀
¿Cómo puedo descargarlo?
A continuación encontrarás los enlaces para descargar la última versión del launcher gratuito para Minecraft LauncherFenix. Todos los archivos publicados en la página son analizados y se encuentran libres de virus pero debido a la extensión de los archivos, puede que el navegador realice una advertencia.
- LauncherFenix-v7.exe: Click aquí para descargar
- LauncherFenix-v7.jar: Click aquí para descargar
Ingresa a nuestro Discord: https://discord.gg/DMpxrWP
Siguenos en Instagram: https://www.instagram.com/launcherfenix/



COMO ARREGLO EXIT CODE -1?? GRACIAS POR SUS RESPUESTAS ;D
Me agregas en discord?
Me agregas en discord?
es muy bueno
NUEVA MODALIDAD RANDOMKITS ENTREN GOGO!!!!!!!!!!!! IP ———> mc.srolemine.com
Aqui les dejo un servidor de MC muy bueno, mas de 300 users online, compatible con 1.7.x hasta 1.21,
tiene modalidades de todas las versiones, RandomKits BoxPvP, survival 1.8 , survival vanilla 1.21, skyblock, skywars, hcf, cubecore, Destruye el nexo,
escapa de la bestia, creativo 1.21, etc todos los modos de juego la ip es: mc.srolemine.com <——————————-
Tambien compatible con Minecraft Bedrock IP: mc.srolemine.com puerto 19132
https://discord.gg/ugZ36kK
7195