
La versión 1.13.1 ya está disponible! Mejora el rendimiento y corrige un montón de errores que se abrieron paso en la versión 1.13. También hay algunos cambios en esta actualización que se enumeran a continuación.
CAMBIOS INTRODUCIDOS
- Optimización del rendimiento.
- Se añadió Coral Muerto.
- Los peces ahora tienen un 5% de probabilidad de perder polvo de hueso cuando mueren.
- Los calamares ahora solo desovan en ríos y océanos.
- Se agregó al juego un concepto de «carga forzada de chunks» y un comando (/forceload) para activar o desactivar dicha carga forzada.
- Se solucionaron muchos bugs que puedes ver más detalladamente en la página oficial, haciendo click aquí.
Fuente: Minecraft.net
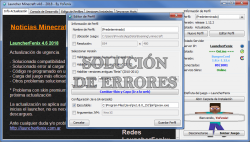
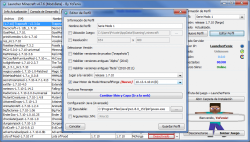
Para obtener la actualización solo debes abrir el LauncherFenix (si no lo tienes puedes descargarlo gratis desde la sección Descargas) y presionar en Jugar! (asegúrate antes de tener seleccionada la versión «1.13.1» en el panel «Editar Perfil»).


https://discord.gg/q5VUj8G
¿Has buscado alguna vez un servidor de Minecraft no-premium en internet? ¿Has visto la cantidad de servidores idénticos que hay copiando a hypixel? Mineverso, único y detergente, te lo hace fácil para que encuentres tu comunidad ideal en el menor tiempo posible. Solo entra a MC.MINEVERSO.COM y elige tu destino. Selecciona en dos clics la modalidad que quieras… y entra. Así de simple 😀
¿Servidor? ––––––––> MC.MINEVERSO.COM
1
1
1
alejandro yo necesito que me pasen minecraft
1
NUEVA MODALIDAD VANILLA ENTREN GOGO!!!!!!!!!!!! IP ———> mc.srolemine.com
Aqui les dejo un servidor de MC muy bueno, mas de 300 users online, compatible con 1.7.x hasta 1.21.4,
tiene modalidades de todas las versiones, RandomKits BoxPvP, survival 1.8 , survival vanilla 1.21.4, skyblock, skywars, hcf, cubecore, Destruye el nexo,
escapa de la bestia, creativo 1.21.4, etc todos los modos de juego la ip es: mc.srolemine.com <——————————-
Tambien compatible con Minecraft Bedrock IP: mc.srolemine.com puerto 19132
https://discord.gg/ugZ36kK
51
Esta web tiene servidores no premium interesantes: https://zonaminecraft.net/
me vale verga pendejo
1
HOLA
1
Hola
1
Hola busco gente para crear un server de minecraft survival 1.20 hasta 1.21
Si estan interesados aqui les dejo mi discord
swo17_
Fue durante un evento de fintech en Montevideo cuando escuché por primera vez sobre uy-bank.com. Un experto en inversiones digitales mencionó cómo esta plataforma es ideal para operar con criptomonedas en Uruguay. Al registrarme en UY Bank Uruguay https://uy-bank.com/ , vi que es una plataforma segura y fácil de usar. Tiene varias herramientas útiles para el trading y la gestión de inversiones. Si estás en Uruguay y buscas una plataforma confiable, definitivamente vale la pena probarla.
1
minecraft download is one of the most popular Minecraft games among crafting gaming applications. This app is full of incredible features and tools.